24x7 Cyber Security Threat Monitoring & Response
Stop attackers in their tracks with our managed cyber security detection and response solution backed by a world-class security operations center.
Endpoint Security
Windows & MacOS event log monitoring, breach detection, malicious files and processes, threat hunting, intrusion detection, 3rd party NGAV integrations and more.
Network Security
Firewall and edge device log monitoring integrated with threat reputation, Whois and DNS information.
Cloud Security
Microsoft 365 security event log monitoring, Azure AD monitoring, Microsoft 365 malicious logins, Secure Score.

powered by RocketCyber’s Managed SOC Platform
and Security Teams
empowered LIVE response by Aegisys 24×7
Cyber threats are 24×7 – Why would your response be 8×5?
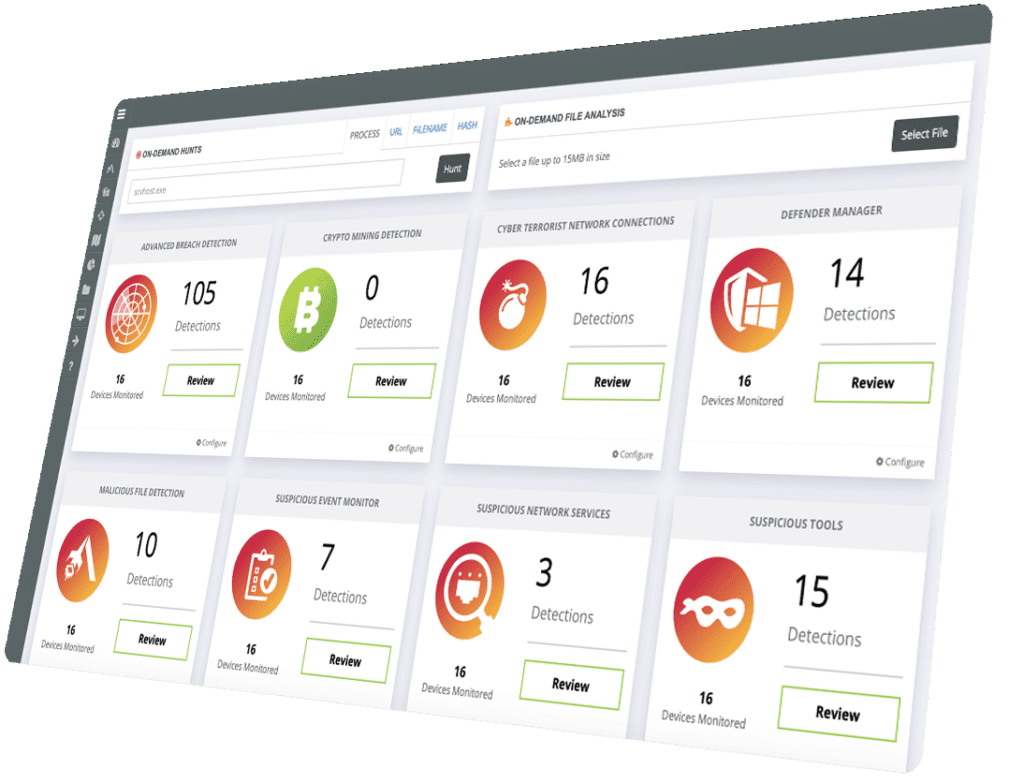
Managed SOC Key Features
The most comprehensive set of Cyber Security features means you can focus you’re your business while our team of security experts ensures the you have the most advanced protection leveraging your existing tools and technologies across endpoint, network and cloud. Aegisys Managed Security Operation Center means we monitor, respond and remediate incidents 24×7.
Security App Store
Get more by monitoring your existing tools 24/7 and with our App Store turn on just the monitoring you want with over 35 cybersecurity Apps across the most popular products including:

- AV/AM Monitoring with SentinelOne, Cylance, Webroot, BitDefender, Windows Defender, Sophos and Deep Instinct.
- Firewall Analyzer & Monitoring with Fortinet, WatchGuard, SonicWall, Sophus, Barracuda, Juniper, Cisco Meraki, PfSense, Untangle, and Ubiquiti.
- Email Monitoring & DNS Monitoring with Microsoft 365, IRONSCALES, Barracuda, DNSFilter and Cisco Umbrella.
-
And much more including …



