Lazy Passwords Are Putting Your Business at Risk Passwords are a pain. No one enjoys trying to remember login credentials for upwards of 100 unique sites and services. More to the point, no one can remember 100+ unique sets of credentials, which leads to all sorts of other awful security problems (don’t worry, we’ll discuss them in […]
Ensuring Data Security in IT Asset Disposal The disposal of old IT equipment is as critical as the implementation of new technologies. Wait, what? It’s true! Particularly when it comes to the secure erasure of sensitive data, proper IT disposal is essential. As organizations routinely upgrade their systems, the need for secure disposal practices is necessary to […]
A Quick and Easy Overview of Cybersecurity Insurance For Your Business In the digital era, cyber insurance has become a critical component of business risk management. As cyber threats evolve, so do the requirements for cyber insurance coverage. This blog explores these changing requirements and why measures like multi-factor authentication (MFA) and endpoint protection are […]
5 Top Cybersecurity Threats: An Executives Guide Business Cybersecurity is serious; an ever-present threat that executives are right to worry about. But understanding the top cybersecurity threats — and the steps your business should take to be more secure — is complex and technical (and let’s be honest, not very interesting for most people). Unfortunately, […]
Car dealerships are increasingly reliant on technology for everything from inventory management to customer relations. However, this means that they face the same, significant challenge that businesses struggle with: cybersecurity. With sensitive data like customer information and financial transactions at stake, it’s especially crucial for dealerships to prioritize robust cybersecurity measures. Read on for the […]
Maximizing the Patient Experience With Top-Notch IT! Let’s put you in the perspective of a patient stepping into a dental office: what’s the first thing you notice? Maybe it’s how modern and clean the space looks or how quickly you can get connected to their Wi-Fi. Or perhaps it’s the opposite, and you find yourself […]
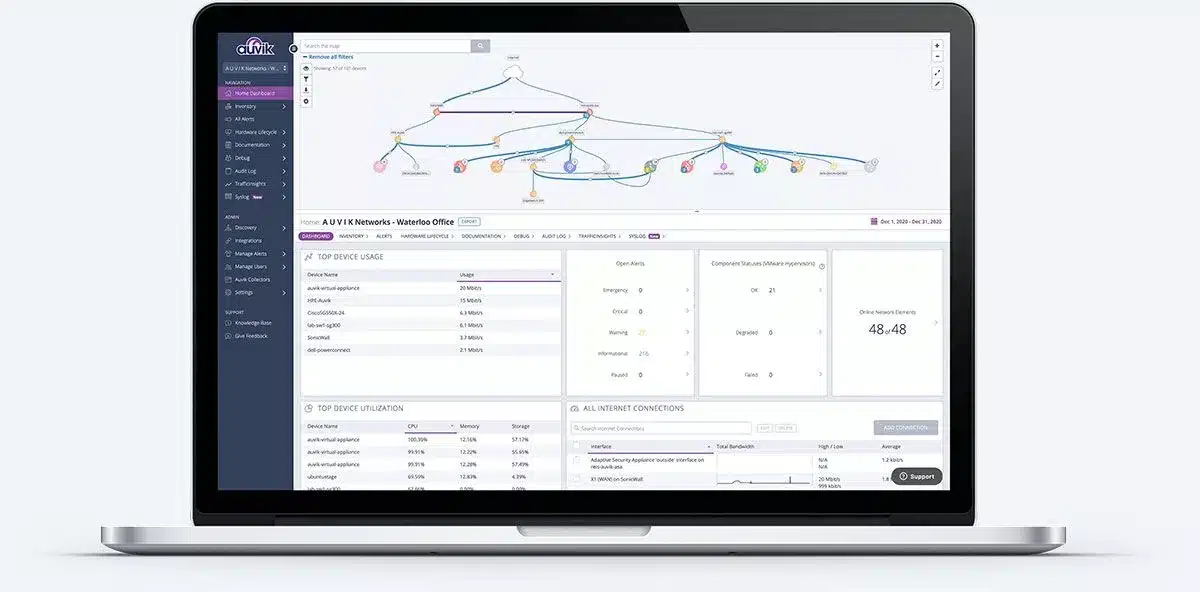
Aegisys Partners with AUVIK to gain true network visibility and control with real-time, automatically updating maps. Transform your network oversight with our feature-rich, cloud-based monitoring solution.
“The only certain thing about IT security is that nothing is certain.” As organizations rely more on information technology and information systems to do business, the digital risk threat landscape expands, exposing ecosystems to new critical vulnerabilities. Risk assessments are nothing new and whether you like it or not, you are in the risk management […]
What is Cybersecurity Awareness Training? Cybersecurity awareness training is a program designed to educate individuals, including your staff, about the various cyber threats and risks that exist in the digital world. It aims to provide them with the knowledge and skills necessary to identify and avoid these threats, as well as to respond appropriately if […]
When a breach happens on the Internet, it’s important to know ASAP so that you can double-check it hasn’t been used against the client already. Proactively protect Your Business from stolen credentials Dark web monitoring is a process of searching for and monitoring information found on the dark web. It finds stolen or leaked information, […]