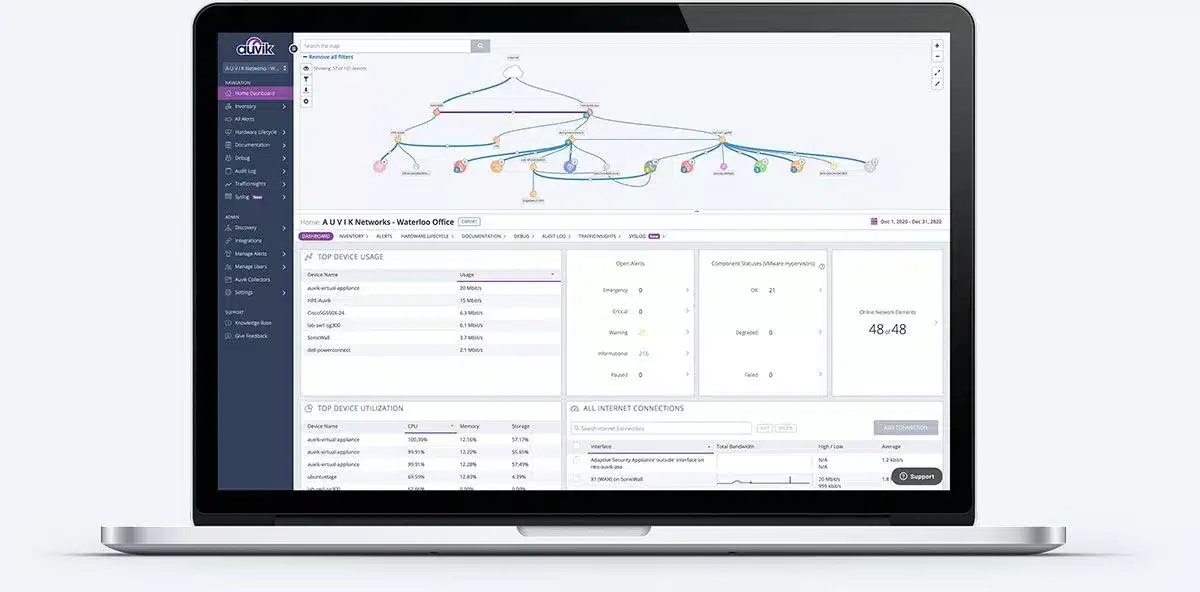
Start CLOUD monitoring your network in under an hour
Most of the Aegisys Auvik solution runs in the cloud, but to access and communicate with your environment securely, we use a collector that runs on your network.
No Hardware is required.
Our lightweight collector is available through an VMWARE OVA installation, LINUX bash installation, or as a lightweight Windows service.

Some Features include:
Identify which applications are being used and if they’re business-critical
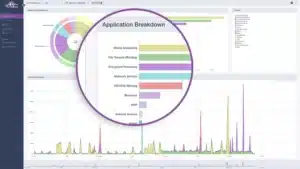
TrafficInsights leverages machine learning and traffic classification to show you which applications—like Dropbox, Netflix, or Slack—or protocols are using up the bulk of the network’s bandwidth so you can confidently make the case for a network upgrade or expansion.
Easily see which devices are hogging all the bandwidth
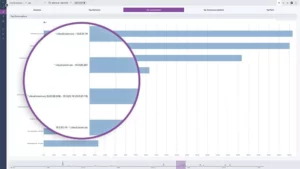
When investigating a network traffic spike retroactively or in real-time, you can immediately identify who’s behind the bandwidth hogging using easy-to-read charts showing top source addresses, destination addresses, conversations, and ports.
See exactly where traffic is going when it leaves the network
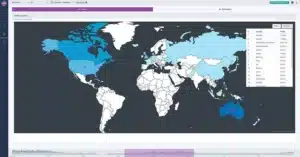
TrafficInsights displays real-time traffic source and destination data in a simple world map. If you identify traffic is being received from or delivered to an unauthorized or unexpected country, you can dig deeper to verify if the traffic is legitimate or malicious, and take necessary steps to protect the network.
We Install, Deploy, Monitor and Mitigate
Aegisys will guide you every step of the way to meet your every need. Our solutions deploy into any network quickly and on budget regardless of your business needs. Want your teams to do the install? No Problem!
Reach out today and get started!



